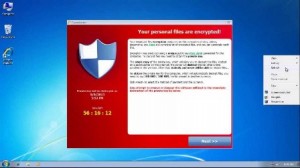
“There is nothing more important than the data” states Dave Simmons, the network administrator with a local Tampa Bay company. That may sound trivial, but the reality is that computers, monitors, printers and network equipment can be replaced but if you do not have a simple data backup strategy in place that includes a single, secondary, or tertiary backup including offsite in multiple geographical locations then you are playing a lose-lose game. One, your data could be lost if there is hard drive crash and two you will probably lose your job depending on what data that hard drive held. Recently we had a client call Infinity Computer Solutions asking if we knew how to decrypt a RSA 2048 virus. As soon as I heard the words RSA I knew it was bad as I had never heard of a RSA virus?! This can’t be good.
What makes this particular malware so nasty is that it truly hijacks your data and demands a ransom for its release! How horrible right? This menacing software aptly named CryptoLocker infects your computer, encrypts your files on your hard drive and will spread to shared files and folders on your network drive! It then pops up a timer on the screen stating you have a certain amount of time to pay up! Now from the movies I watch you typically have a chance to negotiate with the hostage taker but not this time. There is no negotiating, no back room deals, and no games! It’s CryptoLockers way or the highway. So how much do the criminals want? My client reported that they wanted $300 bucks! Did he pay it? Um, no. Did he get his data back, um no. Does he still have a job? Jury still out on that one.
Now if you’re reading this and you’re the IT guy and you have an ache in the pit of your stomach then either one, two, or three things are probably going through your mind. One, if I clean off the virus then maybe the files will decrypt and magically revert back to normal. Survey says, X! Two, maybe if I do a system restore on my computer back to a date previous to the file hostage takeover then everything will be ok. Survey says, X X! Three, OMG I hope the backup ran on the infected computer and/or the network hard drives (but deep down you know that you don’t back up that network hard-drive or network attached storage) but maybe no one will really notice, I can blame someone else and I should still have a job as the IT guy in the morning. Survey says, X X X! FIRED!
Forgive me for my crude Family Feud reference with the X’s but it’s apropos to the conversation at hand. Why, because if your computer or network hard drives are infected with the CryptoLocker ransomware and you have not backed up your files, then you as the IT guy for your company have a lot of explaining to do and a lot of brush up work to do on that resume. So what is the solution to this??? It’s so easy actually.
The bottom line is be proactive, be practical and beyond a shadow of a doubt BACK UP THE DATA or be fired. --Steve Cox

© 2024 TeleVoIPs, LLC
All Rights Reserved